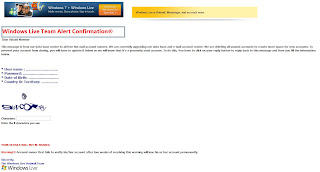
This morning I received an email claiming that the database and email account center for Windows Live would be upgraded. They need to delete all unused account and to make sure that yours won't be deleted, you have to notify the Windows Live team.
Windows Live Team Alert Confirmation
You need to reply with your User name, Password, Date of Birth and Country or Territory. In reality this is a typical phishing campaign for retrieving your login details.
In the last 2 paragraphs it also states:
"YOUR DETAILS WILL NOT BE SHARED"
-> this is to comfort you so you know that your credentials are safe
and
"Warning!!! Account owner that fails to verify his/her account after two weeks of receiving this warning will lose his or her account permanently."
-> This is your typical scare tactic; if you don't do as instructed, your email account will be deleted.
Conclusion
In reality, Windows Live will not send you any emails instructing you to send your password to them so they can verify it is still active. Also, they won't delete your account without a valid reason.
Never reply to these kinds of messages, delete the email and you're good to go.